From Vulnerabilities to Solutions: Harnessing Threat Modeling Tools for Enhanced Application Security
Basics of Threat Modeling
Threat modeling is a proactive approach to identifying potential security threats in an application before they can be exploited by malicious actors. It involves evaluating the security risks associated with software design, infrastructure, and implementation.
What is Threat Modeling?
Threat modeling is the process of systematically identifying, quantifying, and addressing vulnerabilities in an application. It helps organizations understand their potential attack surfaces and prioritize security measures accordingly.Importance of Threat Modeling in Application Security
Threat modeling plays a crucial role in enhancing application security by enabling organizations to anticipate and prevent security breaches before they occur. It empowers development teams to design systems that are resilient to cyber threats.Common Threat Modeling Approaches
There are various threat modeling approaches, including Data Flow Diagrams, STRIDE Analysis, and Attack Trees. Each method offers a unique perspective on the potential threats an application may face.Identifying Vulnerabilities in Applications
To identify vulnerabilities in applications, organizations must conduct thorough risk assessments, identify attack surfaces, and analyze potential threats.
Conducting Risk Assessments
Risk assessments involve evaluating the likelihood and impact of security threats on an application. By understanding the risks, organizations can develop effective mitigation strategies.
Identifying Attack Surfaces
Attack surfaces are the entry points through which attackers can breach an application's security defenses. By identifying these surfaces, organizations can implement targeted security measures to protect their assets.
Analyzing Potential Threats
Analyzing potential threats involves considering the tactics, techniques, and procedures that threat actors may use to exploit vulnerabilities in an application. This information is essential for developing robust security controls.
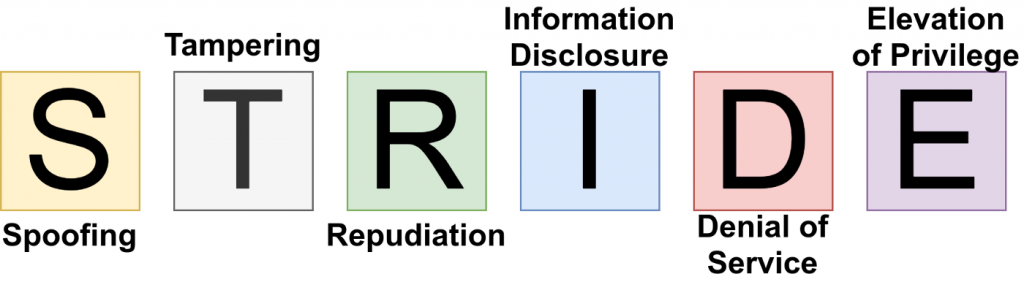
STRIDE Model
The STRIDE model is a framework used in the field of computer security to help identify and categorize the various types of security threats or attacks that a system might face. Each letter in the acronym "STRIDE" represents a different category of threat:
Spoofing: This involves pretending to be someone or something else in order to gain unauthorized access to resources. For example, an attacker might spoof their IP address to appear as if they are coming from a trusted network.
Tampering: Tampering refers to the unauthorized modification of data or systems. This can include altering the contents of a database, modifying the code of an application, or changing configuration settings to disrupt normal operation.
Repudiation: Repudiation involves denying that a certain action took place or that one was involved in it. In a security context, this often refers to a situation where an attacker carries out malicious activities but then denies responsibility for them.
Information Disclosure: This refers to the unauthorized exposure of sensitive information. It can occur through various means such as eavesdropping on network communications, accessing files or databases without proper authorization, or exploiting vulnerabilities to extract confidential data.
Denial of Service (DoS): Denial of Service attacks aim to disrupt the availability of a system or service to legitimate users. This can be accomplished by overwhelming the target with excessive traffic, exploiting vulnerabilities to crash the system, or consuming its resources to the point where it can no longer function effectively.
Elevation of Privilege: This involves gaining higher levels of access or privileges than originally intended. Attackers exploit vulnerabilities to escalate their privileges within a system, allowing them to perform actions that are typically restricted to privileged users.
The STRIDE model is often used during the design and implementation phases of software development to help identify potential security risks and design appropriate countermeasures to mitigate them. Additionally, it can be applied to existing systems to assess their security posture and identify areas for improvement.
Utilizing Threat Modeling Tools for Enhanced Security
Threat modeling tools offer automated solutions for identifying and mitigating security threats in applications. These tools can streamline the threat modeling process and enhance the overall security of an organization.
Introducing Threat Modeling Software
Threat modeling software provides organizations with a platform to visualize, analyze, and prioritize security risks. These tools simplify the threat modeling process and enable organizations to make informed security decisions.
Types of Threat Modeling Tools Available
There are various types of threat modeling tools available, including Microsoft Threat Modeling Tool, OWASP Threat Dragon, and IriusRisk. Each tool has unique features and capabilities that cater to different organizational needs.
Best Practices for Implementing Threat Modeling
Implementing threat modeling best practices involves integrating threat modeling into the software development life cycle (SDLC), training development teams on threat modeling methodologies, and continuously monitoring security controls.
OWASP Thread Dragon
OWASP Threat Dragon is an open-source threat modeling tool developed by the Open Web Application Security Project (OWASP). It provides a platform for creating, visualizing, and managing threat models for software applications. Here are some key features and aspects of OWASP Threat Dragon:
Visual Threat Modeling: Threat Dragon offers a visual interface for creating and editing threat models. Users can draw diagrams to represent the architecture of their software systems, including components, data flows, trust boundaries, and interactions.
STRIDE Model Support: The tool supports threat modeling based on the STRIDE model, which categorizes threats into six main types: Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, and Elevation of Privilege. Users can identify potential threats and vulnerabilities using this framework.
Integration with Other Tools: Threat Dragon integrates with version control systems like Git, allowing teams to collaborate on threat models and track changes over time. This facilitates teamwork and ensures that threat modeling remains an integral part of the software development process.
Customizable Templates: The tool provides customizable templates for creating threat models, making it easier for users to get started with their threat modeling efforts. These templates can be tailored to fit the specific requirements and preferences of different projects and organizations.
Community Support: OWASP Threat Dragon benefits from the support of the OWASP community, which provides resources, documentation, and forums for users to seek help, share experiences, and contribute to the ongoing development of the tool.
Ensuring Sustainable Application Security
To ensure sustainable application security, organizations must collaborate with development teams, integrate threat modeling into the SDLC, and educate stakeholders on the importance of security.
Collaborating with Development Teams
Collaborating with development teams involves involving security professionals in the software development process, conducting security reviews, and promoting a security-centric culture within the organization.
Integrating Threat Modeling into SDLC
Integrating threat modeling into the SDLC ensures that security considerations are taken into account at every stage of the software development process. This proactive approach helps organizations build secure applications from the ground up.
Educating Stakeholders on the Importance of Security
Educating stakeholders on the importance of security involves raising awareness about common security threats, promoting security best practices, and providing training on how to securely handle sensitive data. By educating stakeholders, organizations can create a security-aware culture that prioritizes data protection.
In this comprehensive guide, we have explored the fundamentals of threat modeling and how leveraging the right tools can enhance the security of your applications. By identifying vulnerabilities, addressing security challenges, and ensuring sustainable security practices, organizations can safeguard their assets against potential threats.
Conclusion
Threat modeling tools play a crucial role in enhancing application security by identifying vulnerabilities and providing solutions to mitigate risks. By incorporating these tools into the development process, organizations can proactively address security concerns and build robust applications that protect data and sensitive information. It is essential for businesses to understand the benefits and considerations of implementing threat modeling tools to stay ahead of cyber threats in today's digital landscape. Looking towards the future, advancements in threat modeling tools are likely to shape the evolution of application security, offering new ways to combat emerging threats effectively.
Future Trends and Implications for the Application Security Landscape
As technology advances and cyber threats become more sophisticated, the role of threat modeling tools will continue to evolve. Future trends may include the integration of artificial intelligence and machine learning to enhance threat detection capabilities, automation of threat modeling processes for efficiency, and a shift towards more collaborative and cross-functional security approaches. These developments will shape the future of application security, providing organizations with innovative ways to protect their assets and data from cyber-attacks.
What are the essential steps in incorporating threat modeling tools into the development process?
Organizations should start by defining the scope of the threat modeling exercise, identifying assets to protect, creating threat models, analyzing potential threats, prioritizing risks, implementing security controls, and validating the effectiveness of these measures.How can organizations measure the effectiveness of threat modeling tools in enhancing application security?
Organizations can measure the effectiveness of threat modeling tools by tracking the number of vulnerabilities identified and mitigated, assessing the impact of security controls on reducing risks, monitoring the overall security posture of applications, and seeking feedback from stakeholders involved in the development process.What are some common challenges faced when implementing threat modeling tools, and how can they be addressed?
Common challenges include resistance from teams unfamiliar with threat modeling, lack of resources and expertise, difficulty integrating threat modeling into existing processes, and maintaining threat models over time. These challenges can be addressed by providing training and support to team members, investing in the right tools and resources, fostering a culture of security awareness, and continuously improving the threat modeling practice.
In conclusion, harnessing threat modeling tools is key to strengthening application security and protecting against cyber threats. By understanding the benefits, considerations, and future trends in threat modeling, organizations can proactively enhance their security posture and build resilient applications in today's rapidly evolving digital landscape. Stay informed, stay secure!
References
Shostack, A. (2014). "Threat Modeling: Designing for Security." John Wiley & Sons.
Swiderski, F., & Snyder, W. (2004). "Threat Modeling." Microsoft Press.
Sommer, P. M. (2014). "Threat Modeling: A Practical Guide for Development Teams." Apress.
Microsoft Developer Network (MSDN). (n.d.). STRIDE threat modeling. Retrieved from https://docs.microsoft.com/en-us/azure/security/develop/threat-modeling-tool-threats
Bernstein, D. J., et al. (2017). OWASP Thread Dragon. Springer, Berlin, Heidelberg.
Fruhlinger, J. (2020). "7 keys to a successful application security strategy." CSO Online. Available: https://www.csoonline.com/article/3215864/7-keys-to-a-successful-application-security-strategy.html
Ristic, I. (2013). "Bulletproof SSL and TLS: Understanding and Deploying SSL/TLS and PKI to Secure Servers and Web Applications." Feisty Duck.
Comments
Post a Comment